File Carving
Note: the template was designed for Desktop browsers. Kindly excuse for the display in mobile browsers.
What is file carving?
File carving in literal terms, is the technique of extracting (juicy) files from a given block of (raw) data. This technique is practically used in Digital Forensics to extract important files like pictures, documents, excel sheets, etc.
Steganography
What is Steganography?Steganography in literal terms, is the technique of hiding data in data (say another file) basically to evade surveillance as a matter of privacy.Example: Hiding an image in an image. Its simple like hiding your girlfriend's picture in your picture and all everybody can see is only your picture.
What we are going to deal with in this post?
At first, we are going to see the concept of manual File carving technique(s) then we move on to understand Steganography and practice it a bit, and later we apply file carving technique to try and detect steganography and retrieve the forbidden information from the files to which steganography was applied
Tools of the trade:
HxD – Hex editor
..and let the games begin!
1. As I am dealing with Osama and Obama, lets download one picture each, of both.
2. Now lets use our Hex editor (I am using HxD) to open the file obama.jpg
Look at the first four bytes of data of the image.
Can you see FF D8 FF E0 in hex, or ÿØÿà in ASCII ?
These are called magic numbers or file signature.
A JPG basically has FF D8 FF E0 (E1,E8) in header and ends with FF D9 (ÿÙ in ASCII) in trailer.
Now, if I try to rename obama.jpg into obama.mp3 lets see what happens.
As you can see, the extension-change in the file made it be detected as an audio file by my default mp3 player.
Try playing it?
Obvious error right ? You cannot expect an image to play music for you!
Lets re-open that changed mp3 file with HxD
Do you see the header and trailer of JPG in this 'MP3' file? Can you suspect this MP3 file to be a JPG file?
To validate your assumption, just change the file extension to .jpg and see what it has in store for you.
Else, just open that mp3 file with your default image viewer.
Sounds interesting, right?
This is what any data carving tool actually does. It identifies the file by its signature from the raw data and bounds a file between its header and trailer to save it with the extension associated with it, be it JPG, GIF, MP3, or a .doc file.
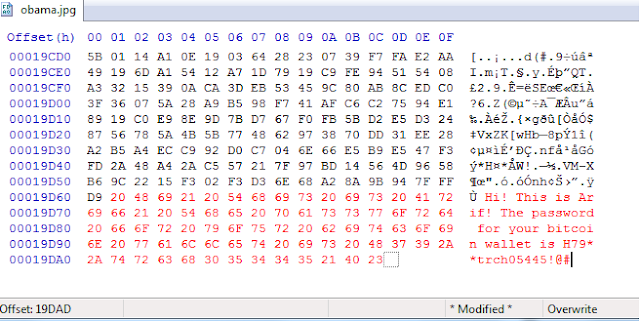
Now, lets try adding some data to obama.jpg - a simple text line will do.
To do it, just open your obama.jpg file in HxD.
At the end of the file, add some content - A statement will do.
Its as simple as follows:
This can be done simply by typing.
(The content in red is what I have added).
Just save the file with any name with extension .jpg
Let me save it with obama.jpg itself.
Lets open obama.jpg with HxD and see what we find.
Voila! We can see that text in the hex data, and even the image opens flawlessly in your image viewers.
This is a basic example of applying steganography to add text in an image file.
Now lets work on a concept where we apply steganography to add image in an image file.
For this lets take two images - obama.jpg and osama.jpg
To-do: Hide osama.jpg into obama.jpg
1. Open both the files (obama.jpg and osama.jpg) in HxD.
2. Hit 'Ctrl + N' to open a new blank window.
3. Copy the whole content from obama.jpg and paste it into the new window
4. Copy the whole content from osama.jpg and paste it at the end of the file in the new window.
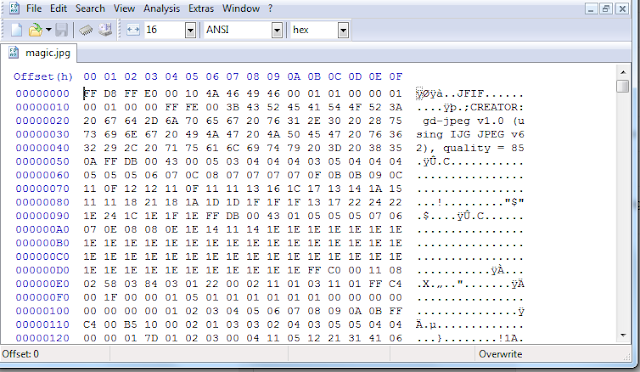
5. Save as magic.jpg
6. Thats it! Now check how the thumbnail looks like in the place where you saved magic.jpg
Do you 'see' the difference between the original obama.jpg and this magic.jpg ?
No! Right? Lets try opening it in your image viewer.
Do you see Osama anywhere in the pic? If you see him, you haven't got good sleep I suppose. ;)
I understand hallucination too! ;)
Simple, right? Now if you ask me where has Osama gone?
File Carving has the answer! :)
Lets apply file carving technique learnt earlier in this post.
1. Open magic.jpg in HxD.
2. Now hit 'Ctrl + F' and type in "ÿØÿà" (without quotes) and hit enter. Hit F3 to find next match.
As you can see in this screenshot, you can find two matches for the text-string "ÿØÿà" - One being the start of the file, and the one shown in this screenshot.
This can simply mean that there are two images in the image we are analysing.
Lets try to retrieve / extract that image data now.
3. Copy the content from the 2nd "ÿØÿà" to the end of the file, or probably till the next "ÿÙ" which marks the end of a JPG file, and paste it into a new blank HxD window.
4. Save the file as 'magic revealed.jpg'
5. Open 'magic revealed.jpg' in your image viewer.
Voila! The magic has been revealed!
This is simple 'logic' behind steganography and File Carving.
Keep exploring, to learn the nuances of increasing the efficiency of File Carving and also to decrypt files on which advanced steganography techniques were applied.
For more details on File signature of various file types, and various other references, visit:
File Signatures (A site by Gary Kessler)
For more details on File signature of various file types, and various other references, visit:
File Signatures (A site by Gary Kessler)
Happy exploring!
Feel free to share your views on this post. Any suggestions to make it better are always welcome.
"Every expert was once a noob!"
Regards,
itsmeRiF
The Logical Kid
The Logical Kid